Can Chromebooks be managed with MEM?
Chromebooks have been hugely popular within the education space these last few years. They are positioned as affordable tablet computers running on Google’s ChromeOS. ChromeOS has a Play Store of it’s own where Android apps can be installed, but also some ChromeOS specific apps.
As these tablets have been imbedded within the educational space for a while, Google is now looking to make it’s way into the Enterprise and this is something I have seen aswell. Within some companies I have seen the following:
- Parents using their children’s Chromebooks to interact with company resources (Mail, Teams…)
- Companies giving out Chromebooks for employees to use, especially during COVID
When employees are using Chromebooks to consume company resources, we need a way to secure this. To test the current MEM support for Chromebooks, I have a Lenovo Duet Chromebook available to tinker with.
Official support statement
Let’s start off with the ‘official’ support for Chromebooks within Microsoft Endpoint Manager. To say it simple, there isn’t any. Support for ChromeOS is an ask that has been around for a long time. There hasn’t been a lot of updates on this particular UserVoice, if not to say none…
So this means that securing your company data on ChromeOS devices isn’t supported through MEM. This doesn’t mean it’s not possible though, during this blog I’ll walk you through a couple of test I did.
Enrollment
During my initial testing, I had hoped that support for a Work Profile like-experience would be supported, because ChromeOS is essentially Android right?
After downloading the Company Portal from the Play Store and logging into my account, all seemed well. But then the limitations for the ChromeOS platform come into play as we have no way of enrolling our tablet. While the Operating System states ‘Android’, it does seem that the Company Portal is aware that this is Chromebook and blocks our enrollment.
Managing ChromeOS with an MDM system is entirely different compared to managing Android devices. Regular enrollment methods such as an Android Work Profile are not supported. So if you want to require compliant devices while still allowing your users to use Chromebooks, you are out of luck…
ChromeOS does have support for multiple profiles to easily switch between a ‘corporate’ and ‘personal’ profile, but Intune does not support this.
App Protection Policies
If MDM enrollment isn’t supported, our only hope is to manage Chromebooks with App Protection Policies and not relying on compliance/enrollment.
As you know, app protection policies are only supported on Android and iOS and when you want to require app protection policies through Conditional Access, you are only able to select those two platforms.
When we check the sign-in logs and look for a sign-in which originated from a Chromebook, we can see that the platform is stated as ‘Android’. This is the same as what we saw in the Company Portal app above.

To test app protection policies, I deployed a App Protection Policy for unmanaged Android devices and configured a Conditional Access policy to require a policy to be active on the device:

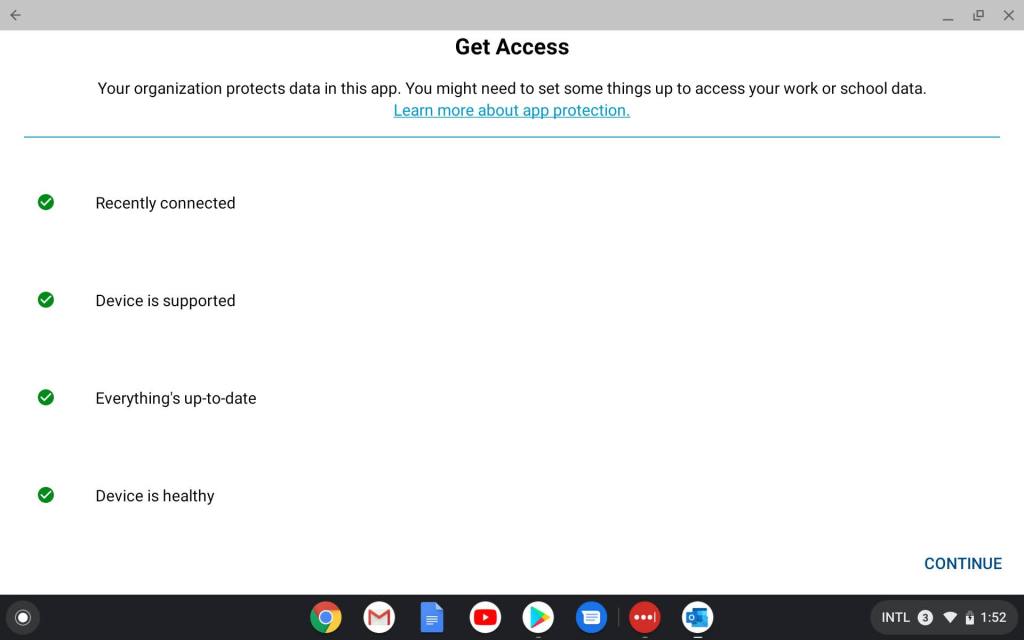
When you login for the first time, you will be prompted to register your device to AAD and comply to the configuration set in the App Protection policies (such as setting up a PIN code).
After this configuration, the app protection is in full effect, things like copy/pasting and saving data to non-corporate locations is blocked.
The only part of app for ChromeOS that does not seem to be supported is requiring approved keyboards. When I had the setting ‘Require approved keyboard’ on, I had no access to my corporate data.
I tried adding the built-in keyboards to the approved keyboard list (com.chromium.arc.ime) and installing Google Keyboard but both didn’t have the right effect. The Google Keyboard would not activate and approving the built-in keyboard did not change anything. So if you want to manage Chromebooks, be sure to disable requiring an approved keyboard or you will be locking these users out.
Update: The correct keyboard to whitelist is org.chromium.arc.ime, thanks
klieby for point that out.
As MAM-WE seems to be functioning on ChromeOS, we can utilize the full functionality for it. Things like doing a selective wipe to remove the corporate data that is lingering on personal devices of an employee is all included in the possibilities.
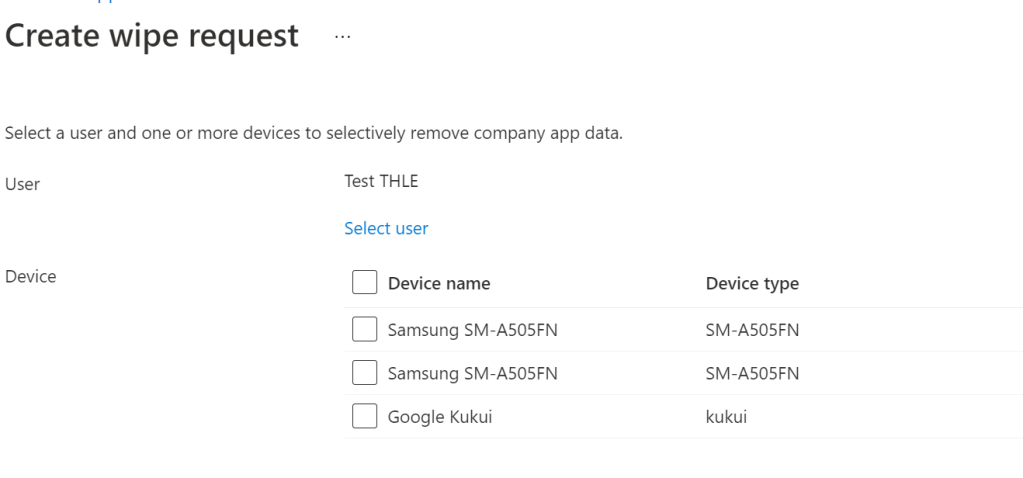
Summary
While it’s nice to see that MEM has partial (unofficial) support for Chromebooks, they still have their work cut out for them. Other platforms such as VMWare’s Workspace One have MDM support for managing ChromeOS built-in.
With the unofficial support for MAM-WE, you can secure your corporate data on these devices but the experience and capabilities leave a lot to be desired.
Categories


Try adding “org.chromium.arc.ime” to the approved keyboard list.
That worked for me.
LikeLike
That does the trick! Thanks a lot, I have updated the blog.
LikeLike
thanks GOD that i reached on your page , that worked for me hurrah!
LikeLike