Creating a dynamic group with all AAD Premium licensed users
Dynamic Groups in Azure AD are truly an amazing feature. It lets you manage a large group of users without the need to manually add every one of them in a specific group.
Some organizations only have AAD Premium licenses for a subset of users, using dynamic groups makes it really easy to scope your AADP policies (like Conditional Access policies) to only the licensed users.
As the documentation says you can use the assignedPlans multi-valued property to create a group based on licenses. The AssignedPlans property has three values:
- capabilityStatus
- service
- servicePlanId
The capabilityStatus is a property that tells us if the the license is enabled. Service is the license name, ServicePlanID is the ID for the license. I suggest always using the ID, as this is less subject to change than the service.
Getting the ServicePlanID
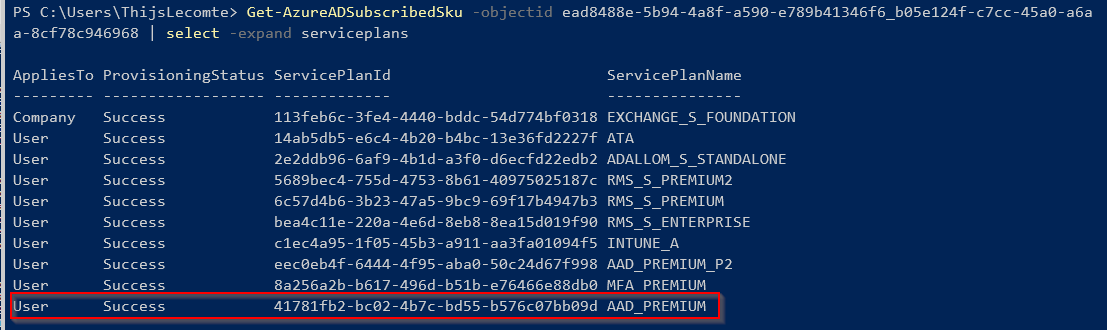
Run the ‘Get-AzureADSubscribedSKU’ command after connecting to AzureAD Powershell. This will return the ObjectID, SkuPartNumber and SkuID of every license you own. Select the correct ObjectID of the license you want and write it down.

Use the ObjectID that you got from the previous command. In the command output, you will find the ServicePlanID.
Get-AzureADSubscribedSku -objectid ead8488e-5b94-4a8f-a590-e789b41346f6_b05e124f-c7cc-45a0-a6aa-8cf78c946968 | select -expand serviceplans
Create the AzureAD group
Navigate to Azure Active Directory (aad.portal.azure.com) and select ‘Groups’.

Select ‘New group’ in the Groups page.

Choose ‘Security’ as the preferred Group Type and choose ‘Dynamic user’ as the membership type. Choose whatever values you would like for the Group Name and Group Description.
Select ‘Add dynamic query’ to configure the query you would like to base this group on.

Use the following rule for a dynamic group based on all AADP licensed users. Use the ServicePlanID you found through Powershell.
user.assignedPlans -any (assignedPlan.servicePlanId -eq "41781fb2-bc02-4b7c-bd55-b576c07bb09d" -and assignedPlan.capabilityStatus -eq "Enabled")

After creating the group, you can monitor the membership processing status and last update date.
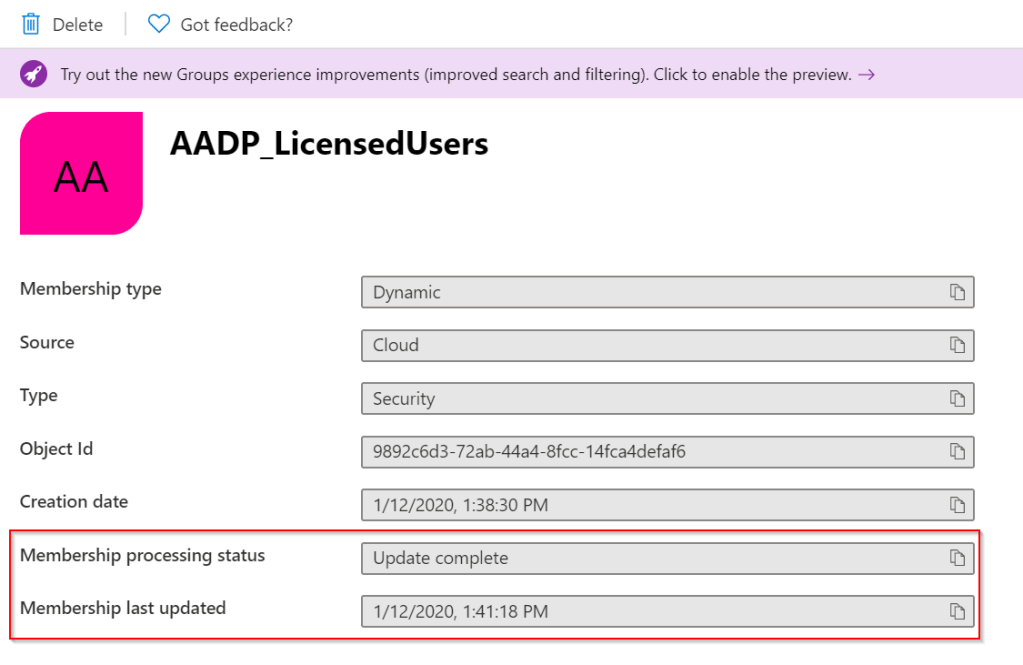
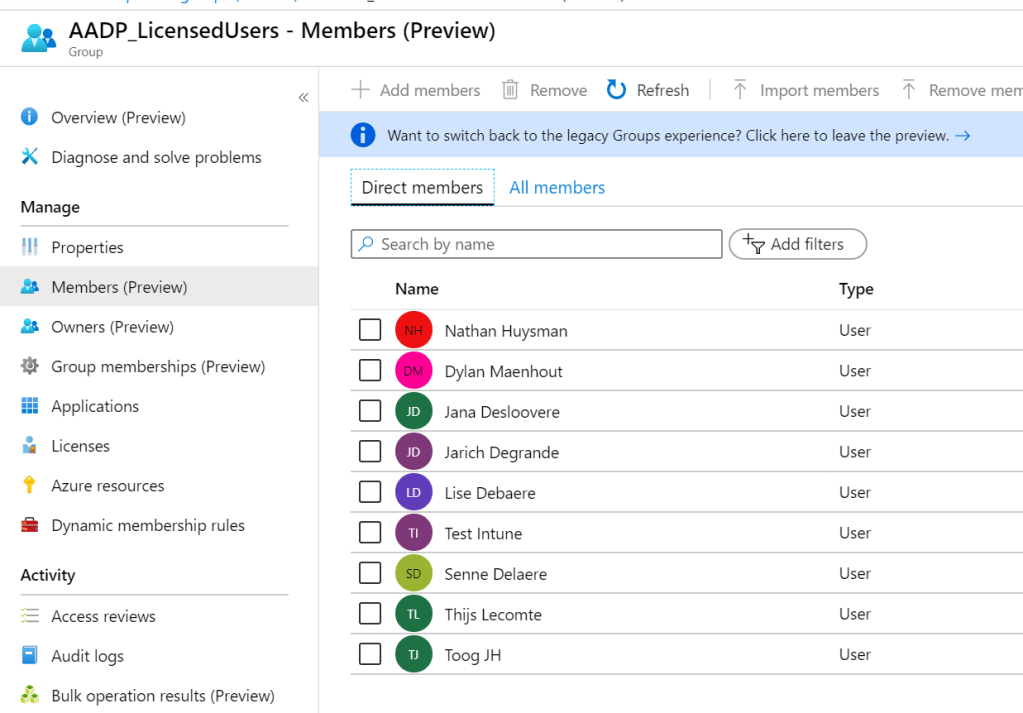
If you wait until the ‘processing status’ states ‘Update complete’, you will find that the group has been populated.
Categories

thanks its working , do you know maybe how i do the same thing expect users that inside other group ?
something like that ….
user.assignedPlans -any (assignedPlan.servicePlanId -eq “41781fb2-bc02-4b7c-bd55-b576c07bb09d” -and assignedPlan.capabilityStatus -eq “Enabled”) execpt users that are inside thing group “groupID”
LikeLike
I am not sure I quite understand you?
Do you want to create a group based on the members of another group?
LikeLike
I think the request is to create a dynamic group based on your described filters, but exclude members of another group.
gma; instead of using the code, you can also manually add filter criteria; this would help to outline how an exclusion may appear in the code underneath; then customise accordingly.
LikeLike
Its not possible to exclude another group. You could exclude certain users through user parameters (like name, department) while using an and statement
LikeLike
Based on the command used, if I wanted to create a dynamic group that adds all users that have an active license on their mailbox, would I just use “user.assignedPlans -any” ?
LikeLike
Just tested this, but that doesn’t work.
AAD doesn’t accept it as it expects another operator
LikeLike
Thank you for the article!
For people who don’t want to open powershell, the ID’s can be found here: https://docs.microsoft.com/en-us/azure/active-directory/enterprise-users/licensing-service-plan-reference
LikeLike
I am very delighted to see the features I have worked are being very useful to customers 🙂
LikeLike
This is very useful and thank you.
I have a question though… how do you exclude certain users from this query, for example, i have some service accounts which are assigned E3 licenses but i only want a list for real human beings. The service accounts still need to have the E3 licenses but the group i am interested in should not include those service accounts. What filter options are there?
Thanks in advance,
George
LikeLike
You could add an and clause to filter on something like job title/UPN. Do the service accounts have something in common to identify them?
LikeLike
The service accounts have email addresses e.g. services@domain.com. I have tried using user.mail or user.UserPrincipalName but i get an error
(user.assignedplans -any (assignedplan.serviceplanid -eq “2789c901-c14e-48ab-a76a-be334d9d793a” -and assignedplan.capabilitystatus -eq “enabled” -and user.mail -ne “services@domain.com”)
The Error is “Failed to save dynamic group. Dynamic membership rule validation error. Mixed use of properties from different types of objects”
LikeLike
Could you try something like this?
(user.userPrincipalName -startsWith “service”) -and (user.assignedPlans -any (assignedPlan.servicePlanId -eq “41781fb2-bc02-4b7c-bd55-b576c07bb09d” -and assignedPlan.capabilityStatus -eq “Enabled”))
LikeLike
I would consider “employee id” if not used already. service accounts can get an employee id and a filter can be done in employee id = blank.
LikeLike
George, the following worked for me:
user.mail -ne “useremail@domain.com” -and (user.assignedPlans -any (assignedPlan.servicePlanId -eq “5dbe027f-2339-4123-9542-606e4d348a72” -and assignedPlan.capabilityStatus -eq “Enabled”))
Best,
Adam
LikeLike
You dont get the m ixed operator message?
LikeLike
Used the following for all users who have AADP 1 OR AADP 2
(user.assignedPlans -any (assignedPlan.servicePlanId -eq “41781fb2-bc02-4b7c-bd55-b576c07bb09d” -and assignedPlan.capabilityStatus -eq “Enabled”)) -or (user.assignedPlans -any (assignedPlan.servicePlanId -eq “eec0eb4f-6444-4f95-aba0-50c24d67f998” -and assignedPlan.capabilityStatus -eq “Enabled”))
LikeLike
Thanks for such a useful piece of knowledge sharing – this is something that is really useful, but not obvious! Especially the commands to dive into the Service Plans – great work!
We’ve used this to create a Dynamic Group and assign this to our Azure AD Self-Service Password Reset policy, using the ‘Selected’ users option and then pointing at this group.
LikeLike
The below worked for me
user.assignedPlans -any (assignedPlan.servicePlanId -eq “70d33638-9c74-4d01-bfd3-562de28bd4ba” -and assignedPlan.capabilityStatus -eq “Enabled”)
Find your SKU here: https://docs.microsoft.com/en-us/azure/active-directory/enterprise-users/licensing-service-plan-reference
LikeLike
hi just wanted to make if I need the opposite of the command?
if I need the disabled or unlicensed users? just change the “Enable” to “Disabled”
LikeLike
That will only show the users who have the license, but not enabled. Not unlicensed users. So you would need to throw the entire query around.
LikeLike
Hi, is it possible to assign certain amount of licenses to particular AD security groups? E.g, I want to assign 100 power app per user license to particular ad group so that individual BUs team should not consume tenant level free licenses only consume what has been allocated to them?
LikeLike
Hi, not this is not possible. It will try to assign as much licenses as possible
LikeLike
Hi,
Thanks for sharing this Article , I am currently trying this in my test tenant to implement it in the Production Tenant. I am currently looking to involve the Dynamic membership rule especially for users having “Enterprise Mobility + Security E5” when I tried the above rule user with AAD Premium P2 License is also listing in the group. Please guide me through this to list only “Enterprise Mobility + Security E5” licensed users only
LikeLike
You need to choose the correct ‘sub sku’ in your license. When using the commands, all features of a license will be returned. Be sure to choose a feature which is only available within an EMS E5 license and not in an AAD P2, such as Defender for Identity for example.
LikeLike